W80X Procedure protection measures for series chips
W80X There are three kinds of program protection measures for series chips: Copy prevention, Firmware encryption, Firmware signature. The use of firmware signature and firmware encryption in addition to copy prevention can further increase the level of protection. The principle of anti-copy is to use the chip Flash Unique ID The uniqueness of the comparison judgment, If you agree, you can keep running the program. In the production burning firmware phase, We call the device to be burned for testing DUT, During firmware burning, The burning tool will read it DUT the Flash Unique ID, Write after encryption Flash the A address, After burning successfully, Device program run time, Read the chip first Flash Unique ID, Read on A Address stored encrypted ID, decrypt, Decrypt and compare the two ID Whether it is consistent, If consistent, Then run the program, If inconsistent, The program is considered to be copied and run, Shut down.
1, Install openssl tool
Requires 1. 0 And above version, It came with it in the folder win 64 position 1. 1 Version installation file, It can also be downloaded from other places. The installation process follows the next step at the prompt point until it is complete.
2, decompression FirmUpdate_2. 2. 0. 8. zip
3, Obtain from the official website SDK
4, Firmware encryption and firmware signing
4. 1 Use CDK Compilation tool
- in tools/W80x/utilities/aft_build_project. sh In the file:
Settings code_encrypt = 1 Indicates that firmware encryption is enabled;
Settings signature = 1 Indicates whether the firmware signature is enabled;
will 5 a openssl. exe Add the corresponding installation path;
Set firmware encryption key parameters, The parameter length is 16 byte, For example, the one used in the figure below is 0~F this 16 A hexadecimal number, while. sh The parameter positions written in the file are corresponding ASCII code; - in tools/W80x/ca/key. txt In the file:
Change the encryption to the corresponding firmware key value, The length is 16 Byte data;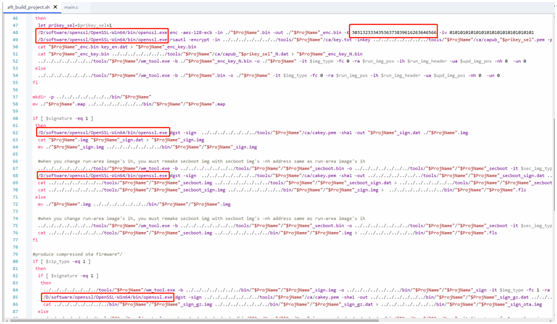
- in tools/W80x/ca/cakey. pem and capub. pem In the file:
cakey. pem is RSA Signature private key, Be used for openssl Signature firmware, capub. pem Yes public key, For unsigning, Replace the contents of both files with your own public and private keys.
4. 2 Use make Compilation tool
- in tools/w800/. config In the file:
Settings CONFIG_W800_IMAGE_SIGNATURE = 1, The firmware signature function was enabled;
Settings CONFIG_W800_CODE_ENCRYPT = 1, Example Enable firmware encryption;
in tools/w800/rules. mk In the file:
Position as shown below, Modify firmware encryption used key, The length is 16 Byte data is converted to the corresponding ASCII Character string;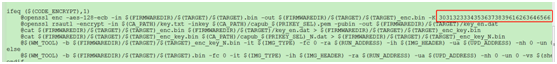
- in tools/w800/ca/key. txt In the file:
Change the encryption to the corresponding firmware key value, The length is 16 Byte data; - in tools/800/ca/cakey. pem and capub. pem In the file:
cakey. pem is RSA Signature private key, Be used for openssl Signature firmware, capub. pem Yes public key, For unsigning, Replace the contents of both files with your own public and private keys.
5, Anti-copy judgment
SDK demo Hit the mark Avoid_Copy_Firm The interface is the reference implementation, The main process is to read the current chip Flash Unique ID, read ID Encrypted data, Decrypt whether the comparison is consistent, If inconsistent, interrupt the program. You can place the interface in mian The starting position or critical path of the function.
There are three places in the example that users can customize, Changes that correspond to the burning tool use case, namely: Decryption mode, Encrypted data storage location, Secret key.
- Decryption mode: The chip provides the function of hardware encryption and decryption, Can realize rc4, aes, des, 3des Encryption and decryption, If other encryption methods are used, You need to implement the relevant decryption function yourself;
- Encrypted data storage location: Need and burn tools AvoidCopyTestCase use-case Location Parameter consistency;
- Secret key: Need and burn tools AvoidCopyTestCase use-case Key Parameter consistency, demo The key is specified in the form of an array, It can also be stored flash In a location to read;
6, Firmware burning
- Copy the compiled firmware to the Burning Tools folder;
- With one's own capub. pem Replace existing files in the tools folder;
- in ToolConfig. ini In the file:
edit TestCaseConfig=AvoidCopyTestCases. xml, The example here is to prevent copying and burning, If there are other test functions required, May refer to "WM_W800 Batch burning tool specific operation guide_V2. 1. doc" Make use case combinations;
Add the device port number to COMS Layout;
Save close, If the tool is open, You need to close the tool and open it again, Configuration takes effect only; - in AvoidCopyTestCases. xml In the file:
The penultimate use case AvoidCopyTestCase The function is to read DUT the Flash Unique ID, With parameters Key Value as the secret key AES128 ECB encipher, Writes the encryption result to the parameter Location Specified location. Needs and procedures 5 The three places correspond:
Encryption mode: The tool uses the encryption mode AES128 ECB, If you want to use other encryption methods, you need to ask for changes to the tool;
Encryption key, The value must correspond to the encryption mode, If you use the default AES128 ECB encipher, So the length of the key is 16 byte, Convert to the corresponding ASCII Character string, In the example, the key is 0~F this 16 The hexadecimal number is converted to the corresponding ASCII Character string;
Save location, Encrypted data storage location. - Revise the last FirmUpdateTestCase The name of the firmware in the use case, Same as the name of the copied firmware, Save close;
unpack FirmUpdate. exe, Select the device port number, Pull down boot (PA0) , press reset, Start burning firmware, A success or failure message is displayed when the burning is complete;
Pull up boot, press reset Reset device, You can verify whether the anti-copy function takes effect.
7, Matters needing attention
If used during the development validation phase FirmUpdate. exe Burned the anti-copy firmware, Later want to burn firmware without copy protection function, Need to modify AvoidCopyTestCases. xml The fourth use case from the bottom WriteSignEnableTestCase Parameter in Enable instead 0, meanwhile WriteDebugLevelTestCase The debugging level is changed to 0, After burning the firmware. Then you can use it Upgrade Tools The tool burns the firmware normally.



studied